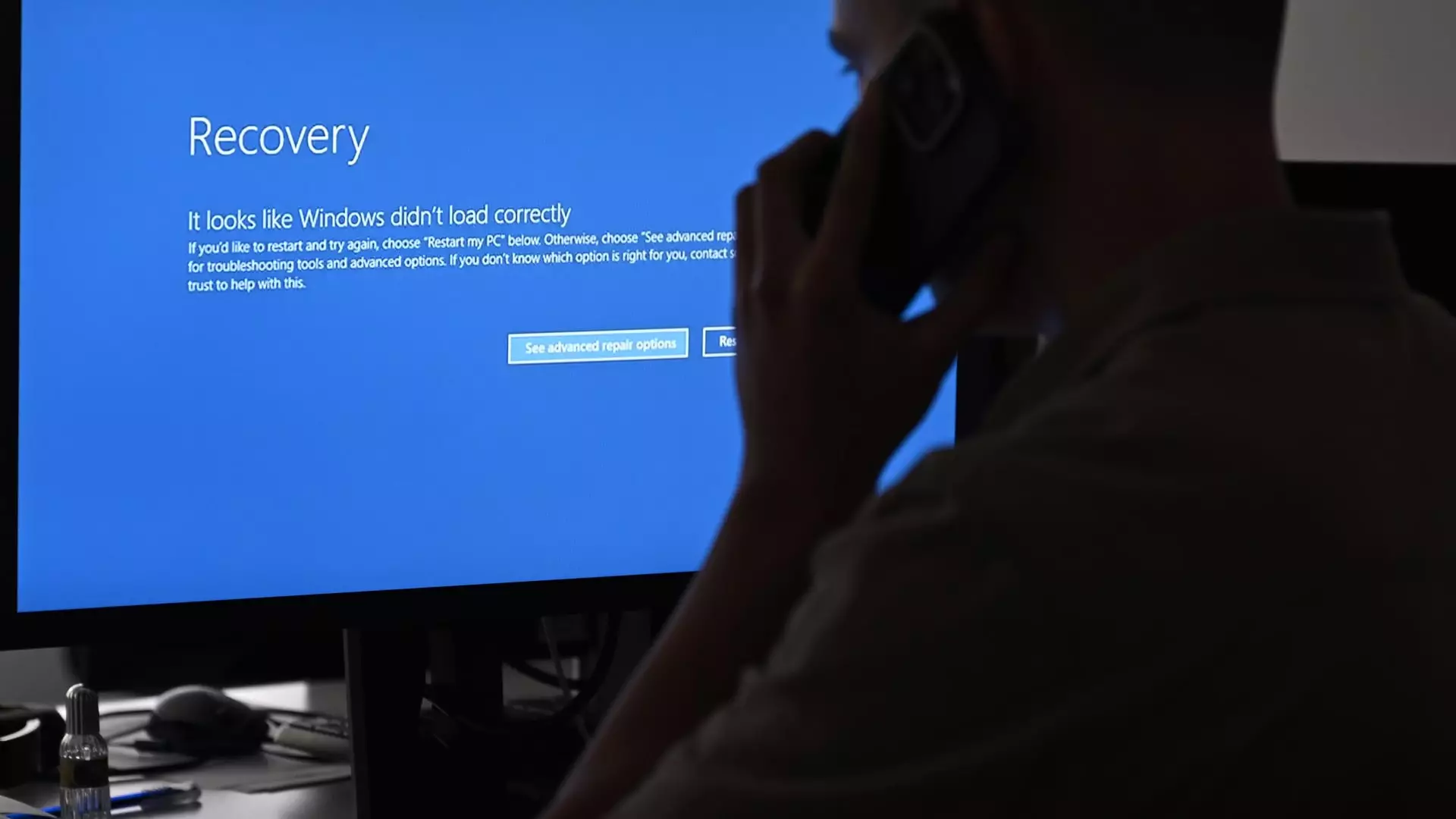
The recent global IT outage caused by a botched software update from CrowdStrike has shed light on the fragile nature of cybersecurity in the modern world. What initially seemed like a cyberterrorist attack turned out to be a content update gone wrong, resulting in widespread disruptions across various industries. This incident prompts a critical examination of the current cybersecurity practices and the need for a more robust approach to safeguarding critical systems and data.
The failed software update from CrowdStrike, specifically tied to the Falcon monitoring software, had catastrophic consequences for businesses worldwide. The update, aimed at enhancing malware detection capabilities, instead caused computers to crash, flights to be grounded, and systems to grind to a halt. The issue stemmed from buggy code being rolled out via an auto-update feature, highlighting the potential risks associated with such automatic deployment mechanisms.
One of the key takeaways from the CrowdStrike incident is the importance of rolling out software updates incrementally. Rather than pushing updates to all customers simultaneously, companies should adopt a phased approach to ensure proper testing and validation. This would involve sending updates to a small group of users first, monitoring for any issues, and then gradually expanding the deployment. Such a method would help prevent widespread outages caused by faulty updates.
In response to the incident, cybersecurity experts stress the importance of building redundancy and resilience into IT systems. A single-point failure, as seen in the case of the CrowdStrike update, should not be able to bring an entire business to a standstill. Companies need to invest in multiple cybersecurity tools, implement thorough testing procedures, and establish clear checks and balances to prevent similar failures in the future.
The CrowdStrike outage serves as a wake-up call for businesses to rethink their approach to cybersecurity. Rather than viewing security services as an unnecessary cost, organizations should see them as essential investments in their future. Cybersecurity should be prioritized, and adequate resources should be allocated to ensure the protection of critical systems and data. This incident underscores the need for a shift in mindset from reactive to proactive cybersecurity strategies.
On a broader scale, the CrowdStrike incident highlights systemic challenges within the cybersecurity landscape. The lack of cybersecurity leadership within organizations, coupled with a general disregard for security as a priority, contributes to the vulnerability of IT systems. There is a need for greater accountability, transparency, and collaboration among stakeholders to address the root causes of cybersecurity failures and prevent future disruptions.
As businesses grapple with the aftermath of the CrowdStrike incident, there is a growing recognition of the need for a more resilient and secure cybersecurity ecosystem. Investing in backup and redundancy, adopting best practices in software development and deployment, and fostering a culture of cybersecurity awareness are essential steps towards mitigating cyber risks. While challenges remain, the CrowdStrike incident serves as a stark reminder of the critical importance of cybersecurity in safeguarding the digital infrastructure of today’s interconnected world.
The CrowdStrike incident has exposed the vulnerabilities inherent in our digital systems and highlighted the urgent need for a paradigm shift in cybersecurity practices. By learning from this event and taking proactive measures to enhance cybersecurity resilience, businesses can better protect themselves against future threats and ensure the uninterrupted operation of critical systems.

Leave a Reply
You must be logged in to post a comment.